SOLUTION
DORA (Digital Operational Resilience Act) Compliance Management
OVERVIEW
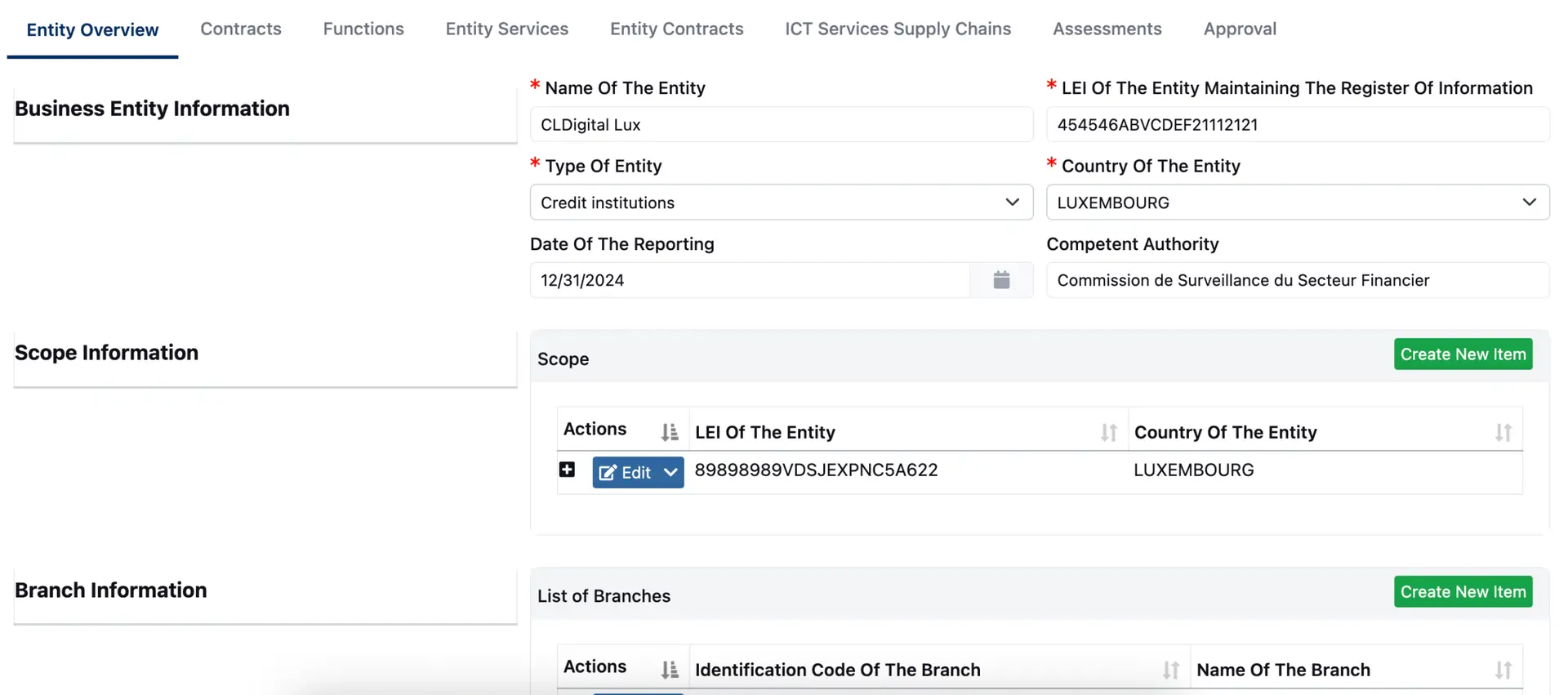
The CLDigital DORA solution helps financial entities across the EU meet the requirements of the Digital Operational Resilience Act with speed, clarity, and confidence. From ICT risk management to incident reporting and threat-led testing, everything is built into a unified, no-code solution that is ready to deploy and easy to scale.
It’s not just compliance. It’s operational resilience with European precision.
Full Visibility
Gain continuous oversight across ICT systems, third-party providers, and critical services to reduce blind spots.
Dependency mapping and integrated monitoring make it easier to see how risks and disruptions impact your operations.
This connected view ensures vulnerabilities are addressed proactively before they create regulatory or operational setbacks.
$200 Revenue Company
“Our business is global and changes daily. The ability to easily move plans and folders within CLDigital with no coding saves us a ton of time every year.”
Chief Information Officer
- Large Insurance Company
- United Kingdom
$200 Revenue Company
“Our business is global and changes daily. The ability to easily move plans and folders within CLDigital with no coding saves us a ton of time every year.”
Chief Information Officer
- Large Insurance Company
- United Kingdom
Regulatory Readiness
Meet DORA’s reporting timelines with confidence by automating detection, classification, and escalation of incidents.
Threat-led penetration testing, audit-ready documentation, and structured remediation workflows simplify regulator interactions and strengthen internal oversight.
BENEFITS
Custom Risk Insights
Gain visibility into ICT risks with customizable workflows.
Resilience Testing
Run resilience tests and scenario-based drills.
Third-Party Oversight
Monitor third-party compliance with oversight and governance.
Automated Submissions
Save time with automated regulatory submissions.
FAQ
Solution FAQs
What is DORA Compliance?
DORA compliance aligns financial institutions with EU regulations for ICT risk management, incident reporting, and resilience testing.
What are the key functionalities of DORA Compliance?
The key functionalities include ICT risk mapping, automated incident reporting, resilience testing, third-party monitoring, regulatory submissions, and structured registers of information.
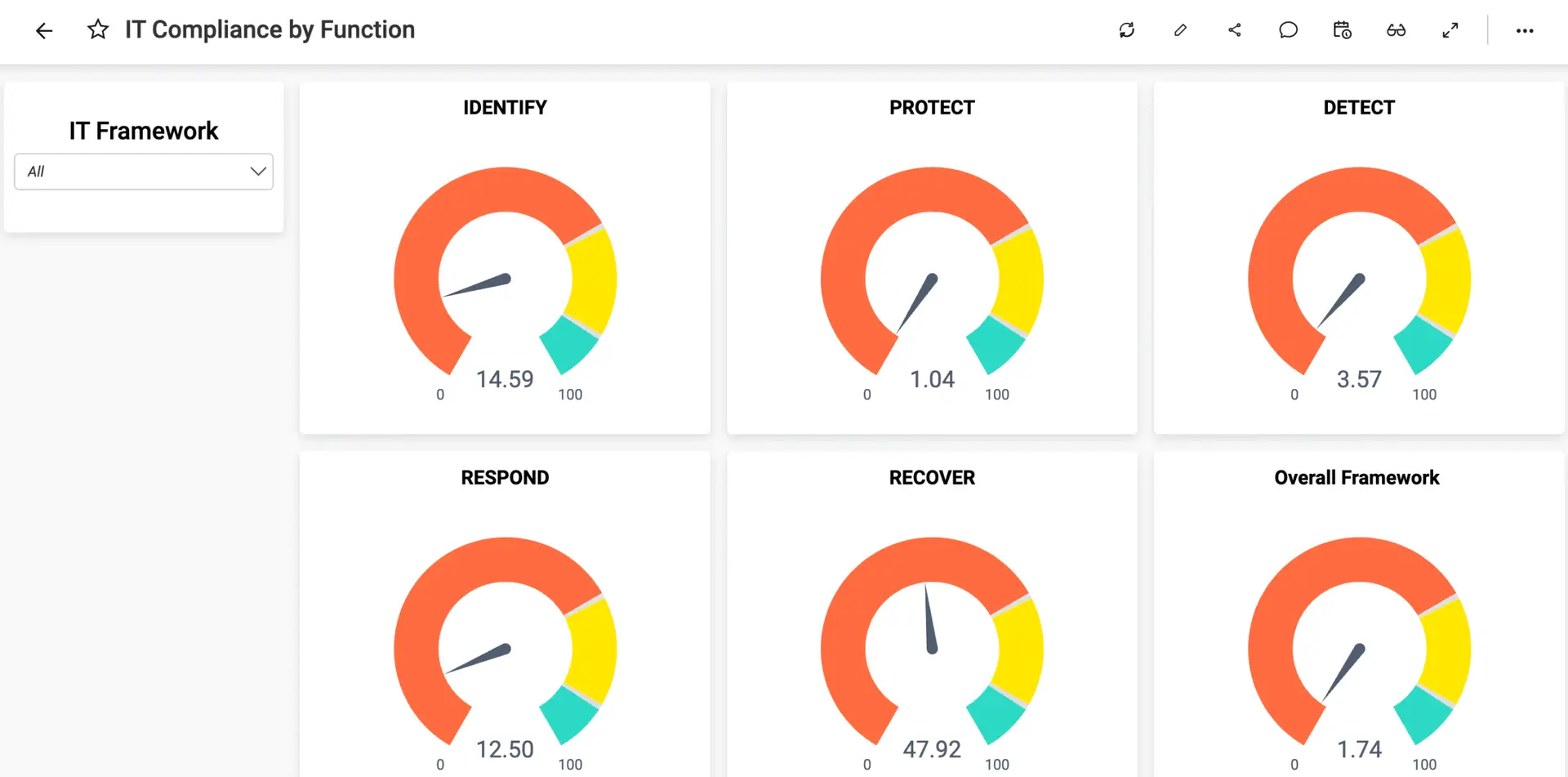
What are the five pillars of DORA?
The Digital Operational Resilience Act (DORA) is a landmark EU regulation designed to ensure that the financial sector can withstand, respond to, and recover from all types of ICT-related disruptions.
Here is an expansion on each of its five pillars:
1. ICT Risk Management
This pillar acts as the core framework for the entire regulation. It requires financial entities to maintain a robust, well-documented ICT risk management system that is integrated into their overall corporate strategy. This includes identifying critical functions, mapping the assets that support them, and implementing continuous monitoring. The goal is to move away from reactive security and toward a proactive stance where risks are identified and mitigated before they can cause systemic failure.
2. ICT Incident Reporting
DORA streamlines the way financial institutions handle and report digital disruptions. Under this pillar, organizations must establish processes to detect, manage, and notify authorities of ICT-related incidents. By creating a standardized reporting template and strict timelines, the regulation ensures that regulators can track emerging threats across the entire financial ecosystem. This collective visibility helps prevent a single localized glitch from turning into a widespread financial crisis.
3. Digital Operational Resilience Testing
To ensure that “resilience” is more than just a buzzword, DORA mandates regular, risk-based testing of ICT systems. This includes basic assessments like vulnerability scans and more complex exercises like Threat-Led Penetration Testing (TLPT) for significant entities. These tests are designed to expose weaknesses in an organization’s defenses under “live” conditions, forcing firms to prove they can actually maintain operations during a sophisticated cyber-attack.
4. Third-Party Risk Management
A major focus of DORA is the “supply chain” of financial services. Since many banks and insurers rely on the same handful of cloud providers and software vendors, a failure at one provider could impact the entire market. This pillar requires firms to conduct deep due diligence on their partners, maintain a register of all third-party dependencies, and ensure that contracts include specific “exit strategies” and service level agreements (SLAs) that align with DORA’s resilience standards.
5. Information Sharing on Cyber Threats
The final pillar encourages a “safety in numbers” approach to cybersecurity. DORA provides a legal framework for financial entities to voluntarily exchange cyber threat intelligence and “indicators of compromise” with one another. By sharing information about new malware or phishing tactics, the industry can create a collective defense mechanism where an attack on one firm helps strengthen the defenses of all others.
What are the benefits of DORA Compliance?
DORA compliance provides full visibility into ICT risks, strengthens third-party oversight, and ensures regulators’ timelines are met.
What are the challenges of DORA Compliance?
Complex reporting requirements, multiple providers, and short incident reporting deadlines increase operational strain and regulatory exposure.
Who needs to comply with DORA?
DORA covers banks, insurers, investment firms, payment and e-money institutions, crypto-asset service providers, and any ICT vendors that support them, regardless of where those vendors are based. When do DORA requirements take effect? The regulation became fully applicable and enforceable on January 17, 2025. Financial entities must be fully compliant by that date.
What are DORA’s incident-reporting deadlines?
DORA requires you to alert authorities quickly: an initial notice within hours of detecting a major ICT incident, a detailed update within one business day, and a final report once the root cause and fixes are confirmed. Exact timeframes will be finalized in technical standards, so build flexible workflows now.
GET STARTED
Let's Connect
Discover how our platform can help you achieve better outcomes and you prepare for what’s next in risk and resilience.